Outsidelessness
Zero is immense
- Feb 13, 2023
- 55
This is another way to securely circumvent any website block. Here's how it works:
Domains are essentially what website handles are (e.g. example.com), and your device needs a numerical IP address in order to connect to these sites. A DNS (Domain Name Server) translates these domains to IP addresses for your device to connect to. A good analogy is your contact list. Your contacts are a list of domains in your name server (Bob, John, Dane ... google.com, youtube.com, bing.com), your specific contact is your domain (Bob ... google.com), and your contact's phone number is the address your computer needs in order to reach the website (Bob -> 800-555-0314 ... google.com -> 142.250.113.138). Therefore, your contact list serves the purpose of making it easier for you to contact people you know without having to remember all of their phone numbers. This is exactly what a DNS server does for your computer, to connect to a website's IP address by using a name that is easy to remember.
DNS is not a secure protocol by itself. Unencrypted DNS requests can be blocked by ISPs, local governments, and other adversaries, who can then monitor your website traffic. Encrypted DNS protocols have been developed to combat this issue, such as DoT (DNS over TLS) and DoH (DNS over HTTPS). These protocols encrypt your traffic and make it indistinguishable from other common connections, so your provider has no choice but to pass it through. By configuring your browser or device to contact a different DNS securely, you can still connect to any website/domain using HTTPS in the clearnet without worrying about censorship or interceptive measures.
This is not to discourage the use of VPNs or Tor, in fact, I encourage their use. However, surfing the internet can't always be done effectively by using VPNs or Tor. If you are still using those services, this configuration can still be a great fallback for you in further protecting your traffic from being monitored.
Here's a little topography showing the difference between using unencrypted DNS and DoH (DNS over HTTPS):
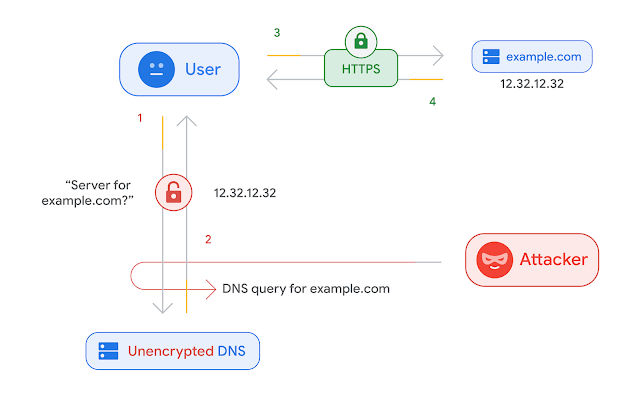
The "Attacker" can represent a hacker, but they can also be your ISP, your government, your hotel WiFi administrator, etc.
If you still need to understand more about how this generally works, this is a great YouTube video explaining DNS:
There are various methods to configure your DNS for browsers and operating systems, including mobile devices. If there is something that hasn't been covered in this thread for your specific situation, you can still search for it and follow the respective guides for your device/browser. Search for "How to set up DoH for <browser/device>".
In this thread, we will be using Quad9, which is a great service for privately handling your DNS requests.
There are a few different Quad9 hostname URLs, but the main ones I suggest are either
Firefox based browsers (Firefox, Mullvad, Palemoon, Basilisk, Librewolf)
Navigate to
Search for "Secure DNS"
Enable "Max Protection"
Change the provider to "Custom"
Input your chosen Quad9 URL
Chromium based browsers (Chrome, Microsoft Edge, Brave)
For Microsoft Edge, put
Navigate to your settings
Search for "Secure DNS"
Turn on "Secure DNS"
Select "With" and set it to "custom"
Input your chosen Quad9 URL. It might complain about it not being a "valid provider", but it will still work completely fine and you can ignore the error message.
Opera & Opera GX
Navigate to your settings
Search for "DNS-over-HTTPS"
Turn on "Use DNS-over-HTTPS instead of the system's DNS settings"
Select "Enter custom provider"
Input your chosen Quad9 URL. If it complains, just check anyway if it's working
Most Android Devices
Navigate to your settings
Select "Network & Internet". There also might be "more connection settings", select that as well
Open "Private DNS"
Turn on "Private DNS provider hostname"
Input your chosen Quad9 URL
Windows 11
Open your settings and select "Network & Internet"
Select your top setting "Should say something like either Wi-Fi or Ethernet"
Scroll down and look for "DNS server assignment" and edit it
Turn on "Ipv4"
Under "Preferred DNS", put 9.9.9.9 for malware protection or 9.9.9.10 for non-malware protection.
Under "Preferred DNS encryption" select "Encrypted only". If on a extremely rare occasion you are attempting to reach a site that isn't inside Quad9's registry, you can easily go back and temporarily enable "Encrypted preferred".
iOS Devices (iPhone, iPad)
Do NOT use Cloudflare. I strongly suggest using Quad9. Cloudflare is known to intercept YOUR data and you should NEVER trust them.
MacOS
Do NOT use Cloudflare. I strongly suggest using Quad9. Cloudflare is known to intercept YOUR data and you should NEVER trust them.
To see whether your DNS connection is working or not, use https://ipleak.net/ and wait a few seconds. In the results, you should see "WOODYNET-1" and nothing else. If that is the case, congratulations! You are securely connected to a name server and you will not have to worry about censorship bullshit. Awesome.
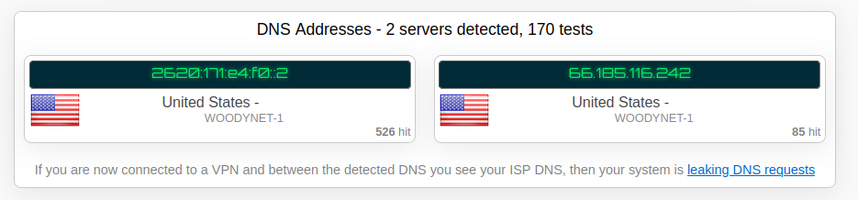
If you are not seeing WOODYNET-1 at all, obviously make sure you've configured your stuff properly.
If you are seeing WOODYNET-1 and other DNS servers at the same time, check your browser and device configurations to make sure they are both using Quad9. If you are using windows 10 or older, you may have to just configure your router to use Quad9 DoH just to save yourself some trouble.
Domains are essentially what website handles are (e.g. example.com), and your device needs a numerical IP address in order to connect to these sites. A DNS (Domain Name Server) translates these domains to IP addresses for your device to connect to. A good analogy is your contact list. Your contacts are a list of domains in your name server (Bob, John, Dane ... google.com, youtube.com, bing.com), your specific contact is your domain (Bob ... google.com), and your contact's phone number is the address your computer needs in order to reach the website (Bob -> 800-555-0314 ... google.com -> 142.250.113.138). Therefore, your contact list serves the purpose of making it easier for you to contact people you know without having to remember all of their phone numbers. This is exactly what a DNS server does for your computer, to connect to a website's IP address by using a name that is easy to remember.
DNS is not a secure protocol by itself. Unencrypted DNS requests can be blocked by ISPs, local governments, and other adversaries, who can then monitor your website traffic. Encrypted DNS protocols have been developed to combat this issue, such as DoT (DNS over TLS) and DoH (DNS over HTTPS). These protocols encrypt your traffic and make it indistinguishable from other common connections, so your provider has no choice but to pass it through. By configuring your browser or device to contact a different DNS securely, you can still connect to any website/domain using HTTPS in the clearnet without worrying about censorship or interceptive measures.
This is not to discourage the use of VPNs or Tor, in fact, I encourage their use. However, surfing the internet can't always be done effectively by using VPNs or Tor. If you are still using those services, this configuration can still be a great fallback for you in further protecting your traffic from being monitored.
Here's a little topography showing the difference between using unencrypted DNS and DoH (DNS over HTTPS):

The "Attacker" can represent a hacker, but they can also be your ISP, your government, your hotel WiFi administrator, etc.
If you still need to understand more about how this generally works, this is a great YouTube video explaining DNS:
There are various methods to configure your DNS for browsers and operating systems, including mobile devices. If there is something that hasn't been covered in this thread for your specific situation, you can still search for it and follow the respective guides for your device/browser. Search for "How to set up DoH for <browser/device>".
In this thread, we will be using Quad9, which is a great service for privately handling your DNS requests.
There are a few different Quad9 hostname URLs, but the main ones I suggest are either
https://dns10.quad9.net/dns-query for non malware-blocking or https://dns.quad9.net/dns-query for malware blocking. The downsides for malware blocking are false positives, hence why I have included non malware-blocking. The IP versions of them are 9.9.9.10 / 149.112.112.10 for no malware blocking and 9.9.9.9 / 149.112.112.112 for malware blocking. You will only be copying those while you configure your connection.Firefox based browsers (Firefox, Mullvad, Palemoon, Basilisk, Librewolf)
Navigate to
about:preferences inside your URLSearch for "Secure DNS"
Enable "Max Protection"
Change the provider to "Custom"
Input your chosen Quad9 URL
Chromium based browsers (Chrome, Microsoft Edge, Brave)
For Microsoft Edge, put
edge://flags/#dns-over-https in your URL and enable "Secure DNS lookups", then continue on. You probably don't have to worry about this if the setting isn't available.Navigate to your settings
Search for "Secure DNS"
Turn on "Secure DNS"
Select "With" and set it to "custom"
Input your chosen Quad9 URL. It might complain about it not being a "valid provider", but it will still work completely fine and you can ignore the error message.
Opera & Opera GX
Navigate to your settings
Search for "DNS-over-HTTPS"
Turn on "Use DNS-over-HTTPS instead of the system's DNS settings"
Select "Enter custom provider"
Input your chosen Quad9 URL. If it complains, just check anyway if it's working
Most Android Devices
Navigate to your settings
Select "Network & Internet". There also might be "more connection settings", select that as well
Open "Private DNS"
Turn on "Private DNS provider hostname"
Input your chosen Quad9 URL
Windows 11
Open your settings and select "Network & Internet"
Select your top setting "Should say something like either Wi-Fi or Ethernet"
Scroll down and look for "DNS server assignment" and edit it
Turn on "Ipv4"
Under "Preferred DNS", put 9.9.9.9 for malware protection or 9.9.9.10 for non-malware protection.
Under "Preferred DNS encryption" select "Encrypted only". If on a extremely rare occasion you are attempting to reach a site that isn't inside Quad9's registry, you can easily go back and temporarily enable "Encrypted preferred".
iOS Devices (iPhone, iPad)
Do NOT use Cloudflare. I strongly suggest using Quad9. Cloudflare is known to intercept YOUR data and you should NEVER trust them.
MacOS
Do NOT use Cloudflare. I strongly suggest using Quad9. Cloudflare is known to intercept YOUR data and you should NEVER trust them.
To see whether your DNS connection is working or not, use https://ipleak.net/ and wait a few seconds. In the results, you should see "WOODYNET-1" and nothing else. If that is the case, congratulations! You are securely connected to a name server and you will not have to worry about censorship bullshit. Awesome.

If you are not seeing WOODYNET-1 at all, obviously make sure you've configured your stuff properly.
If you are seeing WOODYNET-1 and other DNS servers at the same time, check your browser and device configurations to make sure they are both using Quad9. If you are using windows 10 or older, you may have to just configure your router to use Quad9 DoH just to save yourself some trouble.